May 2024
The Digital Operational Resilience Act (DORA) is aimed at improving the EU financial system’s digital and operational resilience. It creates a holistic regulatory framework, harmonising the current patchwork of financial regulations related to information and communication technology (ICT).
DORA covers 21 categories of financial entities (FEs) and ICT third-party providers (ICT TPPs), bringing technology vendors under direct financial supervision. It will apply from January 2025 and the first package of policy products has already been finalised, with the second package due to be finalised in July. DORA’s five key components are:
- ICT risk management
- ICT-related incident management, classification and reporting
- Digital operational resilience testing (DOR testing)
- ICT third party risk management (TPRM)
- Information-sharing arrangements
Understanding the DORA implementation status
DORA builds on existing ICT standards and specifications – however according to a gap analysis performed recently by KPMG, the results suggest that even regulated FEs do not yet meet many of its requirements. Across the EU financial industry, it seems that only one third (32 percent) of regulated FEs comply with all of its requirements, 40 percent partially fulfilling and the remaining not complying at all. It seems that there is still a long way to go for some FEs to expand their compliance programmes.
This same gap analysis also indicates that action is required across all of DORA’s key components – albeit with variations. Due to the existing ICT regulations, FEs typically attain a comparatively high compliance level with DORA’s requirements in the area ICT risk management, including business continuity management (BCM)/IT service continuity management (ITSCM). However, the area of ICT TPRM, covering links with external ICT service providers, still demands considerable attention and action.
Figure 1: Coverage level of DORA requirements
Connect with us
- Find office locations kpmg.findOfficeLocations
- kpmg.emailUs
- Social media @ KPMG kpmg.socialMedia
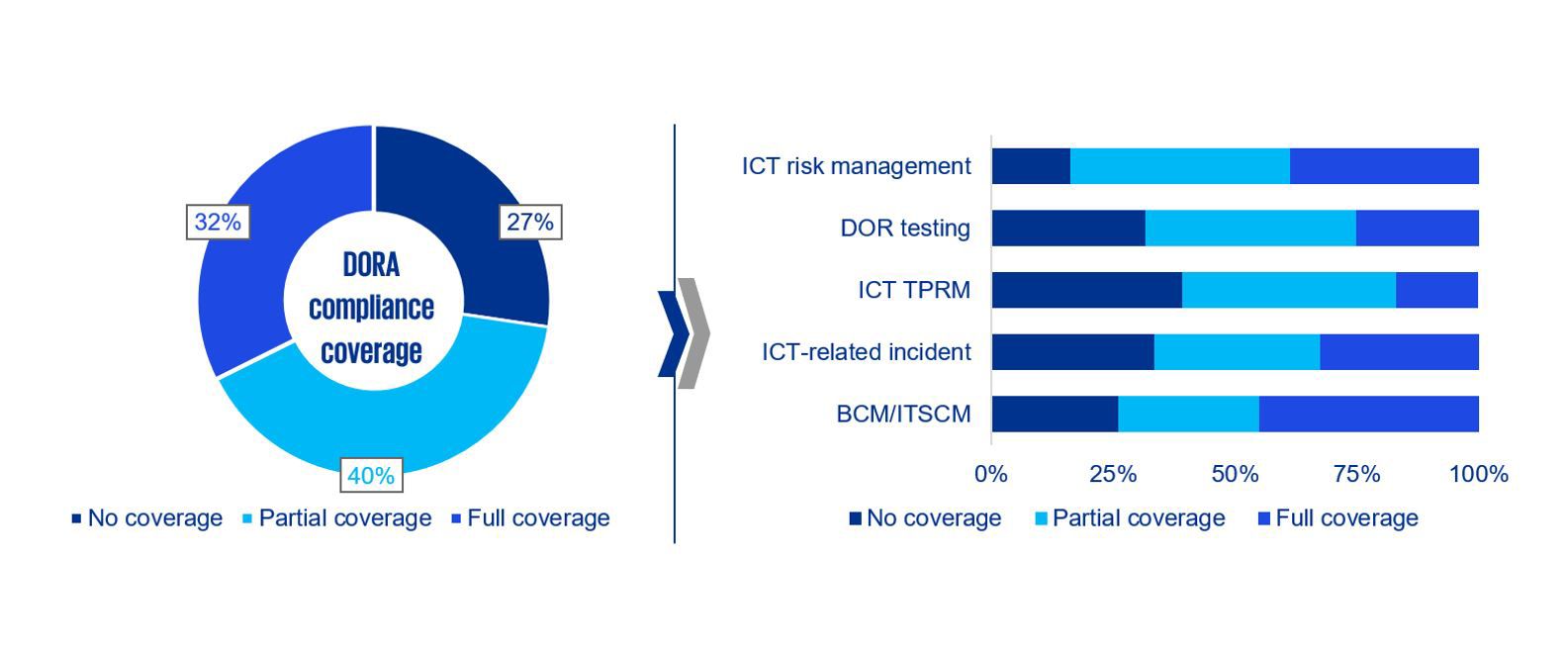
Source: KPMG survey, 2024
Many of DORA’s requirements will be familiar to ECB supervised banks, but they frequently bring a higher level of rigour. A more detailed look at the key components highlights a number of especially challenging areas as follows.
1. ICT risk management (RM)
Existing regulatory requirements for ICT risk management are generally less demanding than DORA. Many FEs’ current ICT risk management frameworks and monitoring capabilities for continual learning and evolving are inadequate to meet the new regulation.
- Response: Banks should build on existing regulatory coverage of DORA’s requirements, establishing a holistic RM approach covering all ICT functions and assets.
2. DOR testing
The testing methods used by FEs fail to sufficiently address threat scenarios and advanced testing of ICT tools, systems and processes based on threat-led penetration testing expected by DORA.
- Response: Banks need to establish an overarching, ongoing, threat-led testing approach for all their ICT assets and implement lessons learned.
3. ICT TPRM
Current industry practices for ICT TPRM fall behind DORA’s stringent requirements in many areas. Common areas of weakness include contract management, holistic TPRM oversight, register of information maintenance, and the management of risk concentration.
- Response: Banks need to implement a dedicated TPRM function within their ICT RM frameworks, backed up by standardised contracts and a tool-enabled register of information.
4. ICT-related incidents
Very few FEs can comprehensively classify ICT-related incidents, and in most cases reporting frameworks are also insufficient to meet DORA’s requirements.
- Response: Banks should develop an integrated, methodical incident classification framework, with interfaces for threat intelligence and incident reporting.
5. BCM/ITSCM
Segregating backup systems from source systems, establishing backup system security and testing the data integrity of data recovery periodically are new DORA requirements.
- Response: Banks can leverage existing measures to build secure, segregated backup systems supported by tool-based record keeping and comprehensive testing concepts.
Implementing a roadmap for compliance
Our experience suggests that most market participants have started to plan and implement the actions required to comply with DORA. Those that haven’t should act immediately. A roadmap for the implementation of DORA should also consider technical standards. FEs face the challenge that the second batch of these standards will only be finalised on 17 July, leaving them just six months for an implementation sprint before the application of DORA on 17 January 2025.
This is a very tight timeline for all regulated entities. Smaller, less sophisticated FEs will typically face the greatest workload, with formal scope reductions limited to the very smallest businesses. Larger FEs with stronger compliance functions and experience of direct ECB supervision have more of a ‘head start’ but will also need to overcome greater complexity.
We see the creation of a central and interdisciplinary resilience function for ICT risk management within the second line of defence as good practice for all FEs. This will help FEs to co-ordinate with other second line functions in the areas of Information Security, BCM and ICT TPRM, to integrate ICT risk management into enterprise-wide risk frameworks, to ensure cooperation between the first and second lines of defence, and to make optimal use of group-wide data and tools.
Anticipating the ECB’s new role
DORA gives a direct legislative basis for the ICT risk management work the ECB has been performing for several years as part of its supervisory activities. In addition, it establishes an oversight framework for critical ICT third-party service providers (CTPPs). Although the ECB will not be directly responsible, it will contribute to new Joint Evaluation Teams (JETs) in charge for on-site inspections at CTPPs. Another new task is the execution of threat-led penetration tests. These new technology-driven tasks require an update of existing methodologies and toolkits.
Banks, whether supervised by the ECB or by National Competent Authorities (NCAs), must monitor supervisors’ plans carefully if they are to prepare effectively for the supervision of DORA compliance. They should also be aware that OSIs focusing on ICT and cyber will be based on DORA from January 2025.
In conclusion, banks and other regulated entities should be in no doubt about the rigour of DORA’s requirements, the need for significant improvements in current frameworks, and the likely levels of scrutiny from supervisors – including an enlarged role for the ECB – commencing in just a few months’ time. A lot of work remains to be done!